Blog Update - December 2023
Howdy, Everyone!
It’s been a really long time since I made a post. This semester was pretty busy, but I’m finally ready to give a quick update.
Things I Learned/Did
- Continued to work updating Sambot, my OpenAI Discord bot.
- Competed in NCL for the first time (I placed #243, hopefully I can improve that rank next year!)
- Played some CTFs with TAMU and friends. Recently, we won 3rd in TUCTF which was pretty cool. 🙂
- Explored Canarytokens, which I planned to write about but decided against it as they have amazing documentation already. In short, they are a quick and dirty (but very robust!) solution to intrusion detection which can be deployed in pretty much any application instantly.
Life Updates
I finally got my first job in cyber (Yippee!) but I am still looking for a summer internship. Getting As in my classes has sapped up most of my free time, but I am excited to be back for winter break. Right now I am planning on learning some C++ and contributing to one or two web apps that I really enjoy.
Random CTF writeup (Not Detailed)
As I mentioned earlier, ret2rev (TAMU) participated in TUCTF 2023 and placed 3rd. I didn’t solve a lot of the challenges as we got carried (thanks, flocto) but I did solve this challenge involving using pwntools to crack a treasure chest.
The challenge was called “Bludgeon the Booty” and the goal is to rotate 3 wheels in order to crack the treasure chest.
I wrote a pwntools script that solved it via complete search, and this was my first time officially solving a CTF challenge with pwntools.
1 | from pwn import * |
It’s pretty clear how the script works so I won’t take the time to explain it (plus this is mainly meant as a general update post!) but recvuntil was a new thing for me which was pretty cool. You may also notice the code attempts to reconnect and continue where it left off, which ended up not working as the combination on the chest resets when the connection is lost. In the end, I didn’t get to solve this challenge as the TUCTF infrastructure was very unstable, and my school’s WAF was also not super enthusiastic about my netcat connections so I kept getting reset. However, I asked a team member to run the script and they got the flag for me!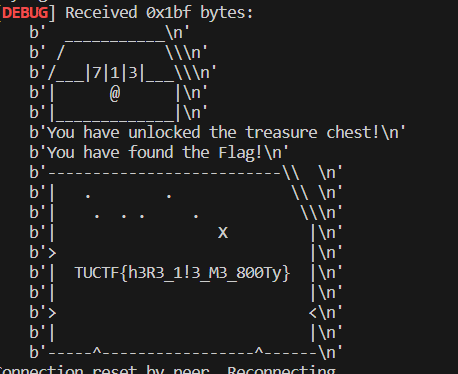
Goodbye for now!
